No products in the cart.
Why is your website still getting hacked even though you've added Cloudflare protection? ? The culprit may be this DNS configuration vulnerability! Today we are going to introduce the Cloudmare artifact, like a ‘Cloudflare detector’, 3 steps to pull out the misconfigured source IP!

Why is your website still getting hacked even though you've added Cloudflare protection? ? The culprit may be this DNS configuration vulnerability! Today we are going to introduce the Cloudmare artifact, like a ‘Cloudflare detector’, 3 steps to pull out the misconfigured source IP!
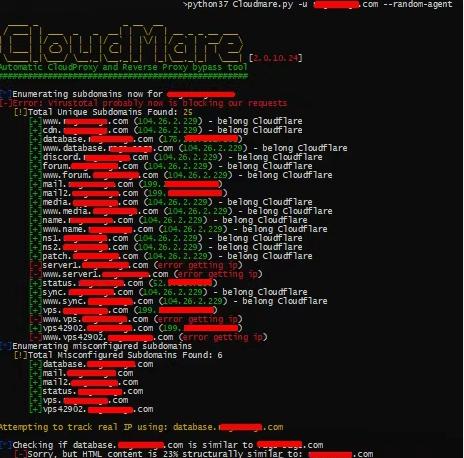
(The schematic has been desensitised, feel free to eat ~)
This open source tool can detect in one click:
✅ Cloudflare/Sucuri/Incapsula protected sites
✅ DNS resolution misconfiguration
✅ Source server real IP exposure risk
? Five minutes to get started
1️⃣ clone arsenal
git clone https://github.com/MrH0wl/Cloudmare.git
cd Cloudmare?It's understandable to the uninitiated: it's like downloading a toolkit to your computer!
2️⃣ Enable scanning mode
python Cloudmare.py -u 你的网站.com --bruter -sC?Advanced tips: add -sSh parameter can also detect SSL certificate vulnerability Oh!
3️⃣ View the results of the battle
Report Interpretation Guide:
?Red warning → must be fixed immediately
?⚠️ yellow warning → optimised configuration recommended
?Exclusive guide for Android users
Turn your phone into a hacker with Termux (tutorial lite):
Install the ‘Hacking 3-Piece Kit’:
pkg install git python dnsutils
One click to run:
git clone https://github.com/MrH0wl/Cloudmare.git cd Cloudmare && python Cloudmare.py -hh
?Tips: the first run to be patient and wait for the tool to automatically load the plug-in Oh ~ ~
? Important Notes
Only authorised testing, illegal use of the consequences!
Don't panic when you encounter bugs: click here to submit an issue!
Support Windows/Mac/Linux, but Python must be ≥3.7.
? Protection self-checklist
✔️ Regularly run Cloudmare to check your own website.
✔️ Disable non-essential DNS resolution records
✔️ Source site IP binding access whitelisting
✔️ Enable Cloudflare's ‘strict mode’